By: Ralph Santitoro | January 27, 2021

SD-WAN services have evolved networking to focus on what is important for organizations, namely, applications and policies. Rather than working with low level networking constructs and functions such as IP packets and access control lists (ACLs), SD-WAN services enable network administrators to focus on creating policies for the specific applications used in the business, e.g., Office365, instead of its IP address, e.g., 52.165.129.203. This also simplifies setting policies per application such as which applications to allow or block, prioritize based on business importance and readily identify applications using the application name rather than a nondescript, obscure IP address or port number.
Since SD-WAN services typically use the public Internet network as one or more of its WAN connections, some basic security functions are required, e.g., a stateful firewall providing IP port and protocol filtering, domain name filtering, network and port address translation (NAT/PAT), etc. This approach no longer provides sufficient protection for users, devices and applications for three key reasons:
- Application migration to the cloud
- Users connecting from anywhere
- Accelerating volume of threats
Application Migration to the Cloud
As part of organization’s digital transformation, applications have steadily migrated from running ‘on-premises’ in an organization’s data center to running in the cloud. This means that users will no longer predominantly connect to their applications via a private network, e.g., MPLS, to the data center but will more commonly connect to the cloud via a public Internet connection. According to the Gartner 2019 report “Future of Network Security Is in the Cloud”, more workloads (applications) are running in the cloud using cloud computing (infrastructure-as-a-service or IaaS) or consumed via software-as-a-service (SaaS) than running or consumed in the organization’s internal data center.
Users Connecting from Anywhere
Users have been connecting from anywhere rather than within the confines of an organization’s office building. The network perimeter, from which users connect, has vastly expanded due to the COVID-19 pandemic with many users connecting from home. This perimeter has been growing for several years with users connecting their laptops or smartphones remotely from the office. Furthermore, the number of users who use their own devices a.k.a. BYOD (Bring Your Own Device) has also significantly increased over the past several years. Such assets, not owned by the organization, cannot be controlled, e.g., the organization cannot limit which applications can be installed which subsequently introduces cybersecurity challenges. Just as users are no longer required to connect to the network from the office, organization must adapt to support more devices that are user owned.
Accelerating Volume of Threats
Business is booming for threat actors as we all have seen from the successful ransomware attacks that have shut down businesses and municipalities until payments have been made. While there have been several high profile payment card breaches over the past few years, ransomware attacks have also increased which have an immediate impact to business continuity. Organizations need to think of such breaches as they do trying to recover from a natural disaster, e.g., hurricane, where they have the disaster recovery processes in place for a cybersecurity attack similar to how they would restore business operations in the event of a natural disaster.
An increasing number of tools are becoming available to automate the production of threats so individual people are no longer needed to create and delivery various threats as this is often done now using artificial intelligence (AI) and machine learning (ML) software. Threat prevention needs to be continuous and adaptive to not only protect against currently known threats but also protect against evolving and unknown threats outpacing the rate in which the threats are created.
Increasing Importance of Cybersecurity
When the network perimeter was confined to an organization’s office buildings, i.e., users, devices, and applications operated within the building and private network, cybersecurity was manageable. Now that the perimeter is boundless, each organization’s cybersecurity policies, architectures and frameworks must be revisited and be an integral part of their network architectures and implementations. The network can no longer be designed independently from cybersecurity considerations. Furthermore, cybersecurity can no longer be considered separately from organizational processes and technologies. Cybersecurity must be woven into the fabric of an organization. Hence the importance of SASE.
What is SASE?
SASE melds the comprehensive WAN capabilities of SD-WAN with a comprehensive set of cybersecurity functions to address the migration of applications to the cloud, users working from anywhere, and the accelerating volume of threats.
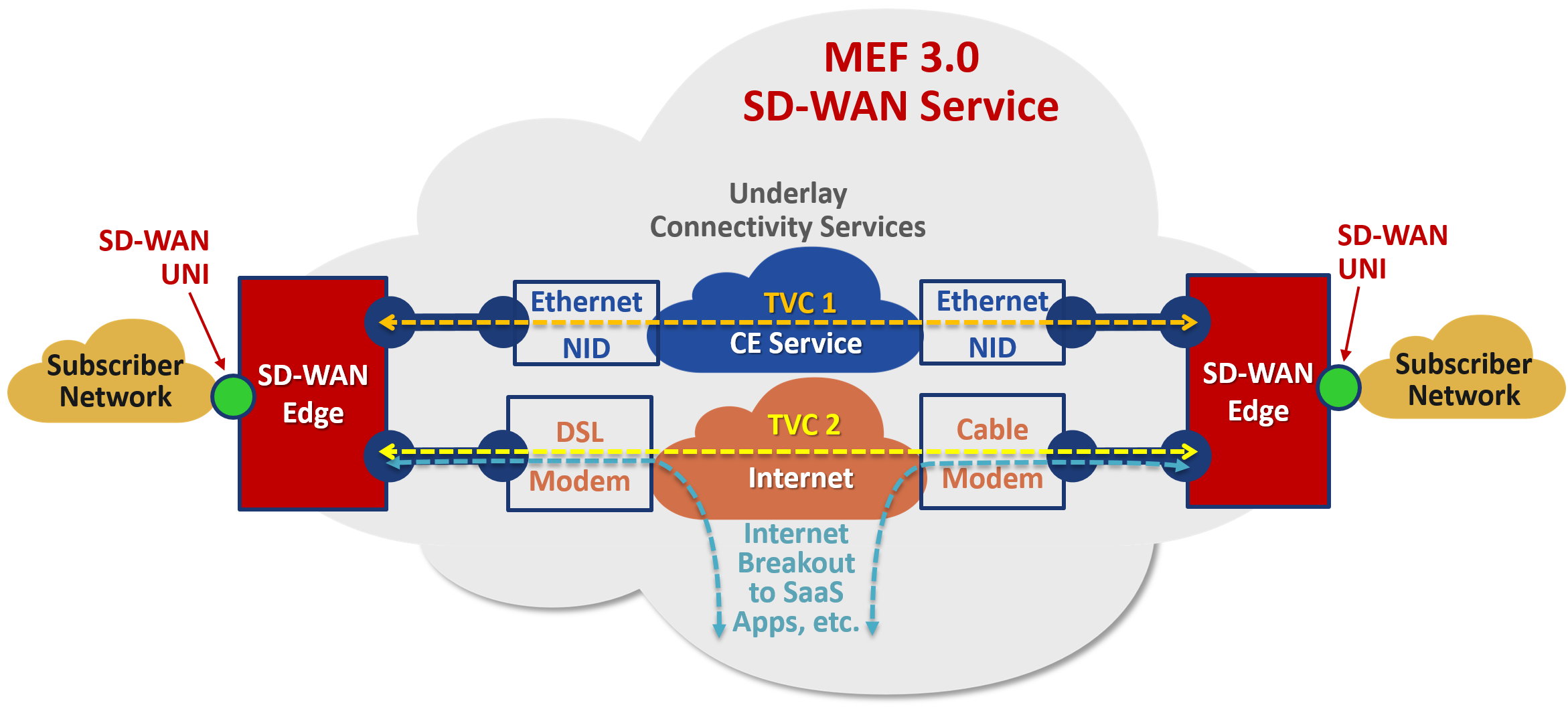
Typical SD-WAN capabilities provided by SASE Services
SASE services utilize capabilities commonly provided by SD-WAN services listed below.
- Over-the-top (OTT) service
- Operates over any type of underlay connectivity (WAN) service, e.g., broadband, MPLS, LTE, etc.
- Inherent High Availability
- SD-WAN services typically deployed over two or more underlay connectivity services, e.g., MPLS + Broadband
- Secure Transport of Application Flows
- SD-WAN services encrypt all IP packets in transit over underlay connectivity services
- Supports Multiple Virtual Topologies
- Can construct unique topologies based on application requirements, e.g., hub & spoke, full mesh, etc.
- Application-aware networking
- SD-WAN services enable users to focus on business applications, e.g., Office365, Zoom conferencing, Skype call, etc. rather than IP packets
- Policy-based networking
- Provides intent-based policies and policy actions, e.g., allow, block, or prioritize, to determine how IP packets associated with each application are treated by the network rather than defining ACLs using low level, obscure network constructs
- Encrypted Internet Breakout to Cloud-based Applications and Services
- Connects to public cloud services and SaaS applications via encrypted TLS (HTTPS) or IPsec VPN tunnels
- Application Flow Cybersecurity Functions
- SD-WAN services typically provide an integral set of foundational cybersecurity functions. Such functions include:
- Stateful firewall
- Network/port address translation (NAT/PAT)
- IP Address, Port Number, and Protocol Filtering
- Domain name filtering (block known malicious domain names or quarantine those with a bad reputation)
- Security middlebox function to decrypt encrypted application flows to apply security policies and then re-encrypt
- SD-WAN services typically provide an integral set of foundational cybersecurity functions. Such functions include:
Note that some of the aforementioned Cybersecurity functions are part of Secure Web Gateway (SWG) functionality which provides protection against web-based threats. As SD-WAN services and solutions evolve to SASE, they continue to incorporate more cybersecurity functions.
Typical Cybersecurity capabilities provided by SASE Services
SASE services add additional cybersecurity functions to the aforementioned foundational cybersecurity functions provided by SD-WAN services.
- Security Policy Management
- Provides intent-based policies that define policy actions, e.g., Allow, Block, Quarantine, or Sandbox, to apply to IP packets associated with an application
- Malware Detection and Removal
- Identify, clean (then allow) or remove (block or quarantine) malware from application flows
- URL Filtering
- Block or Quarantine suspicious (or known to be malicious) URLs for an allowed domain name
- Data Loss Prevention (DLP)
- Identify and block application flows containing confidential, sensitive, privacy-related and personally identifiable information (PII), e.g., social security numbers, drivers license number, payment card numbers, biometric information, etc.
- Anti-Phishing
- There are many types of phishing attacks, some of which may be addressed via other security function such as URL Filtering, Malware Detection, and DLP
- A phishing attack uses social engineering to entice the user to click on a URL or submit PII via what appears to be a legitimate email
- Threat Detection, Prevention and Response
- Using AI and machine learning, identify suspected threats based on anomalous behavioral patterns, block the threats or threat actors, and subsequently monitor and report them to a security information and event management (SIEM) system
- Note that this functionality appears under different names in the industry:
- EDR (Endpoint Detection & Response)
- NDR (Network [Intrusion] Detection & Response)
- TDR (Threat Detection & Response)
- XDR (Extended/Cross Layer Detection & Response)
- NIDS/NIPS (Network Intrusion Detection System/Network Intrusion Prevention System
- IDS/IPS (Intrusion Detection System/Intrusion Prevention System)
- Identity Management
- Identify the different users, devices and applications that want to access the network or networked resources for use by access control policies and mechanisms.
- An organization will often use several Identity Providers (IdP) for identity management (IdM). IdM may be performed internally and via external 3rd-party IdPs.
- It is important to consider a federated approach to IdM to ensure security policies can be effectively managed and controlled when your organization uses a multiple cloud providers
- Adaptive Access Control
- Ability to modify security policies that determine the amount of access a user, device, or application is granted ranging from full to partial to no access
- Continuous Threat Monitoring
- The continuous monitoring of application flows from users, devices, and applications wanting to access the network and networked resources to identify anomalous behavior
Note that the first six aforementioned cybersecurity functions are commonly provided by a cloud access security broker (CASB) service and may also be provided by services using terms such as NGFW (next generation firewall), UTM (unified threat management), and ATP (advanced threat prevention/protection). The last three functions listed are part of a Zero Trust Framework (ZTF) which provides least privilege access to users, devices and applications. Zero Trust cybersecurity functions play a key role in SASE services.
Cloud-based SASE Security Services
There are many reasons to use cloud-based SASE security services versus using premise-based SASE security services.
- Easier and quicker to Deploy
- Setting up a cloud-based SASE security service only requires you to do two things to begin using the service.
- Setup a primary and secondary IP VPN connection from your WAN router or SD-WAN Edge to the SASE security service
- Enter your SASE security service account credentials
- Setting up a cloud-based SASE security service only requires you to do two things to begin using the service.
- Simpler and More Cost Effective to Scale Up or Scale Down
- SASE security services leverage cloud infrastructure so you can scale up or scale down just like you do with other cloud-based services such as AWS EC2 cloud compute services where you can, in minutes, add or remove compute capacity
- Stop Internet-based Threats before they reach you
- A cloud-based SASE service sits between you and the Internet so you are protected from Internet-based threats before they reach your site, device or application
Premise-based versus Cloud-based SASE Services
Since a network perimeter continually changes as users now work from anywhere, you must ensure that the WAN and cybersecurity functionality is sufficiently flexible to support this new reality. Whether a user is connecting from an office, at home, at an airport, at a hotel, etc., they need the same level of threat prevention wherever they connect. When away from the office, users will connect via the Internet using broadband, Wi-Fi or LTE/5G cellular data services. A cloud-based service enables a common approach for these use cases.
From the office, a user may connect to the organization’s data center via a private network connection, e.g., MPLS VPN, in addition to connecting to the public Internet. For the private network, premise-based SASE cybersecurity functions are sensible and could be centralized at the data center as well as distributed at each office. However, some organizations run all of their applications in a virtual private cloud or via a cloud-based SaaS offering all connected via the Internet in which case, a cloud-based SASE cybersecurity service may be more appropriate.
Some parts of a SASE service require functionality to be performed on premises, specifically where the users are located. SASE services could be provided via software installed on the personal device or by a SASE device on premises. Below are some examples that necessitate SASE functions to be located on premises.
- If your business location uses multiple WAN connections (since the WAN connections terminate on premises)
- If you need to provide threat prevention over the private network between business locations
- If you need to protect internal networked resources from threats that could be introduced by personal devices (BYOD)
The need for on premises SASE services will diminish as more applications migrate from on premises servers to the cloud and more users work from anywhere and connect via the Internet.
What makes up a SASE Service?
SASE services currently consist of a both WAN and cybersecurity functionality as previously discussed. However SASE services are evolving to also support LANs, Wi-Fi, and Endpoints (IoT devices, laptops, smartphones, etc.).
You might ask “Is there a minimum amount of WAN and cybersecurity functionality for something to be called a SASE service?”. Unfortunately, because of the lack of an industry-accepted or standardized SASE service definition, different offerings are referred to as SASE services. For example, is the WAN connectivity part of the service limited to a single IP VPN or can it also support multiple underlay connectivity services such as Dedicated Internet Access (DIA) + MPLS or broadband + LTE, over which SD-WAN virtual connections (SWVCs) operate and provide additional network resiliency? Often the aforementioned cybersecurity functionality is packaged in different service offerings. Just as it took a few years (plus MEF Forum standardization) before SD-WAN services had a well-defined, baseline set of functionality, SASE services will take a few more years to achieve such baseline functionality.
The Need for Industry Clarity around SASE
While no industry standard exists for SASE, MEF Forum is developing a new standard “MEF W117 SASE Service Attributes and Framework” to augment its other related standards work on SD-WAN and Cybersecurity including the industry’s first SD-WAN service standard, “MEF 70 SD-WAN Service Attributes and Services“, “MEF W88 Application Flow Security for SD-WAN Services”, and “MEF W118 Zero Trust Framework and Service Attributes” – the latter two currently under development. These standards will play a key role in providing clarity in the marketplace.
Conclusions
Many services and products use the term SASE to define their offerings and without an industry standard, capabilities vary widely. This lack of standardization makes it challenging to evaluate different offerings and requires that you understand the different WAN and cybersecurity functions to ensure they address your organization’s business objectives for digital transformation. Given the many SD-WAN and cybersecurity options, don’t hesitate to reach out to industry experts to obtain guidance to help you make the optimal choices for your business.
About the Author
Ralph Santitoro has expertise that spans the assessment, definition, design, integration, operations, marketing, and sales of multi-vendor solutions and managed services using Edge Cloud, SD-WAN, SASE, Zero Trust, Cybersecurity, Private 5G, and Work-from-Home technologies that facilitate the enterprise digital transformation. Ralph is a founding member of MEF Forum where he developed the industry’s first SD-WAN standard and is leading a new standard developing a comprehensive Zero Trust Framework to continuously protect users, devices and applications from threats both known and unknown.
In 2014, Ralph was awarded the Distinguished Fellow title at MEF Forum for his outstanding, long time leadership and contributions to shape the telecom industry. In 2016, he was awarded the MEF Excellence Award for Best Consulting Practice. In 2018, Ralph was named one of the top 25 movers & shakers in the telecom industry by Fierce Telecom Magazine and in 2020, he was awarded the MEF Outstanding Contributor award for SD-WAN leadership and the driving force behind SD-WAN standardization. Ralph also co-authored 4 books and regularly lectures on leading-edge technology topics at industry events.